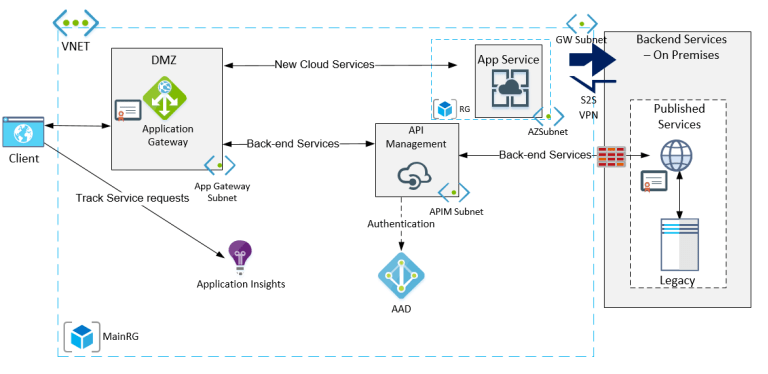
Some time ago i wrote up a post (located here) explaining how you can setup traffic manager with ADFS and have proper monitoring of the service. Today i will go over how to setup ADFS behind the Azure Application Gateway. This will enable you to protect your ADFS service and monitor it with the WAF provided by the application gateway.
Before we begin one prerequisite which i am still not sure if its really needed but i had problems and i believe this fixed it:
You need to set the default HTTPS Binding, i believe this is required as i am not sure if the health probe is truly SNI compliant, i might be wrong here but it doesn’t hurt to set this. To set it you simply need to run the following command on the WAP servers (just change the cert hash):

Azure Load Balancer
Azure: Renewing the SSL Certificate of the Azure Application Gateway. Always a hassle changing out certificates, think of ADFS and WAP:). Dec 01, 2016 The new HTLM5 client capability supports neither the Azure AD Application Proxy or the AD FS Web Application Proxy, which is mind-boggling. It's not all darkness tho, RDS MI, in preview, is the key to solving this (or so it seems), since it aims to bridge the gap between legacy logon (RDS) versus modern (conditional access/MFA etc).
Sep 14, 2011 We are converting a ASP.NET Web Application to Azure. The Authentication process is handled using LDAP call in the existing code, but we are planning for ADFS integration. The ADFS server already exposing the claims to Microsoft Federation Gateway to consume by other applications. The easiest way to setup an ADFS farm 2016 or 2019 in any of the cloud environments – Azure, AWS or Google GCP is to use our publicly available images in the cloud marketplaces. Setup ADFS Farm 2016 in Azure Deploy a Microsoft ADFS 2016.